When connecting or accessing to remote computer or server with Remote Desktop Connection (RDC or “Terminal Services”) client (mstsc.exe) through Remote Desktop Protocol (RDP), the authentication when logging in with a user account with blank password or no password may fail. The Remote Desktop Connection client may return “The user name or password is incorrect” error even if the credentials provided is valid and correct.
Or, the following error message may be display:
Logon failure: user account restriction. Possible reasons are blank passwords not allowed, logon hour restrictions, or a policy restriction has been enforced.
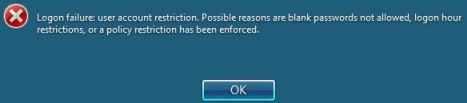
Above error message may also happen on other scenarios. For example, when attempting to authenticate and sign in to web page on website hosted on Microsoft Internet Information Services (IIS) server. The error happens even though the user ID is a valid account, but mostly on user account with blank password.
When the error happens, Event Log will have entry under System log similar to below:
The server was unable to logon the Windows NT account ‘Computer_Name\User_Name’ due to the following error: Logon failure: user account restriction. Possible reasons are blank passwords not allowed, logon hour restrictions, or a policy restriction has been enforced. The data is the error code.
For additional information specific to this message please visit the Microsoft Online Support site located at:
http://www.microsoft.com/contentredirect.asp.For more information, see Help and Support Center at http://go.microsoft.com/fwlink/events.asp.
The error happens because in Windows operating system such as Windows XP, Windows Vista, Windows 7, Windows Server 2003 and Windows Server 2008 (or their R2 versions) does not allow local user to log on remotely via network logon if the user account does not have a password set.
Thus, in order to resolve and fix the “Logon Failure: User Account Restriction” issue, user will need to configure and set the remote system to explicitly allow local user account with blank or no password to be used for network logon. To change the policy, perform the following steps on the remote computer (which is connected to):
- Open Local Group Policy Editor by typing gpedit.msc in Start Search box and hit Enter.
- Navigate to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options branch.
- Locate and double click on Accounts: Limit local account use of blank passwords to console logon only option.
- Select the radio button for Disabled to allow user account with blank (or no password) for remote login.
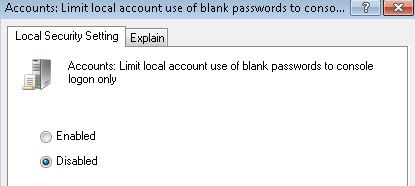
- Click OK.
For user on system without Local Group Policy Editor, follow the Registry Editor alternative:
- Run Registry Editor (RegEdit).
- Navigate to the following registry key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\
- Double click on LimitBlankPasswordUse registry value name, and set its value data from 1 to 0.
- Close Registry Editor.
The above error message may also occurs when user connects to network shared folders based on files sharing service on Windows XP workgroup. In such case, the main culprit or reason that causes the problem is due to the user account used to sign into the remote network shared files and folders does not have permissions to access or read the folder and its content. To resolve this issue, make sure the user account used to authenticate when connecting to network share has the right permissions to the shares. To view and modify permissions, right-click on the folder and select Properties, and go to the Sharing tab to click the Permissions button.
Recent Posts
- Able2Extract Professional 11 Review – A Powerful PDF Tool
- How to Install Windows 10 & Windows 8.1 with Local Account (Bypass Microsoft Account Sign In)
- How to Upgrade CentOS/Red Hat/Fedora Linux Kernel (cPanel WHM)
- How to Install Popcorn Time Movies & TV Shows Streaming App on iOS (iPhone & iPad) With No Jailbreak
- Stream & Watch Free Torrent Movies & TV Series on iOS with Movie Box (No Jailbreak)
 Tip and Trick
Tip and Trick
- How To Download HBO Shows On iPhone, iPad Through Apple TV App
- Windows 10 Insider Preview Build 19025 (20H1) for PC Official Available for Insiders in Fast Ring – Here’s What’s News, Fixes, and Enhancement Changelog
- Kaspersky Total Security 2020 Free Download With License Serial Key
- Steganos Privacy Suite 19 Free Download With Genuine License Key
- Zemana AntiMalware Premium Free Download For Limited Time